
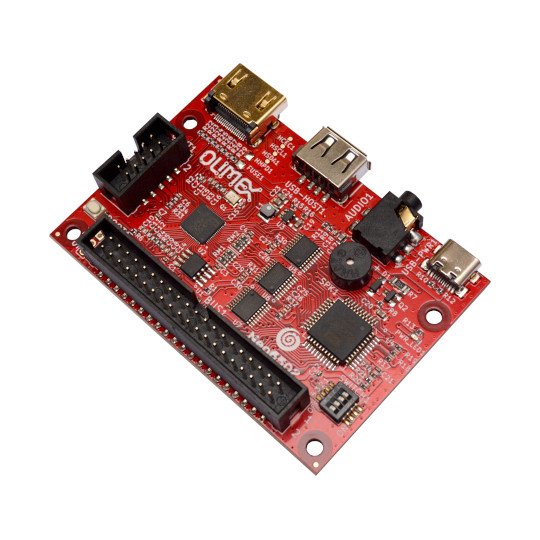
ESP32-POE2 is modification of the popular ESP32-POE but capable to deliver up to 25W power from PoE connection. This opens up lot of more possibilities.
User selectable 24V / 0.75A or 12V / 1.5A is provided plus +5V/1.5A for external circuits.
From software side ESP32-POE2 acts exactly as ESP32-POE so all software will work on both.
Some of the ESP32-POE2 features are:
- ESP32-WROOM-32 – WiFi and Bluetooth module
- Low power design – 200uA consumption in deep sleep
- Ethernet 100Mb interface with IEEE 802.3 PoE support
- USB-C connector for power and ESP32 programming
- MicroSD card working in 1 bit mode
- LiPo battery charger with LiPo battery connector
- Battery level monitor pin on ADC
- External power supply detection pin on ADC
- Provides 24V/0.75A or 12V/1.5A to external circuit
- Provides 5V/ 1.5A to external circuit
- UEXT connector
- EXT1 connector
- User button
- Reset button
- PCB dimensions: 59×90 mm
The ESP32-POE2 price start from EUR 16.76 for 50+ pcs order.
The board is designed with KiCad and all files are available at GitHub.
ESP32-POE2 is supported by all the popular platforms Espressif SDK, MicroPython, ESPHome, PlatformIO, Arduino.




















Recent Comments